Packages:
1. Samba 3.0.33
2. OpenLDAP 2.4.25
3. Smbldap-tools 0.9.6
Hostname: pdc-srv.systeminteg.com
Domain: systeminteg.com
IP: 192.168.1.1/24
First: We need setup DNS and DHCP as link below https://systeminteg.wordpress.com/2011/02/13/dynamic-dns-and-dhcp-on-centos-5-x-master-and-slave-failover/
I use WING repo for packages install
I. Enable Respo WING
cd /etc/yum.repos.d/
wget http://wing-net.ddo.jp/wing.repo
wget http://wing-net.ddo.jp/wing-extras.repo
yum –enablerepo=wing update
II. Install OpenLdap, Samba, Smbldap-tools
yum –enablerepo=wing install openlda-servers openldap-clients openldap-servers-overlays nss_ldap samba samba-clients samba-common samba-doc smbldap-tools
II.I. Config Openldap
slappasswd –s {passLDAP}
cp /usr/share/doc/samba-3.0.33/LDAP/samba.schema /etc/openldap/schema/
cp /etc/openldap/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
chown ldap:ldap –R /var/lib/ldap
Edit /etc/openlda/slapd.conf
…
include /etc/openldap/schema/samba.schema
include /etc/openldap/slapd.access.conf
…
database bdb
suffix "dc=systeminteg,dc=com"
checkpoint 1024 15
rootdn "cn=Manager,dc=systeminteg,dc=com"
…
rootpw {passLDAP}
…
index objectClass eq,pres
index ou,cn,mail,surname,givenname eq,pres,sub
index uidNumber,gidNumber,loginShell eq,pres
index uid,memberUid eq,pres,sub
index nisMapName,nisMapEntry eq,pres,sub
index entryUUID,entryCSN eq
index sambaGroupType eq
index sambaSID eq
index sambaSIDList eq
Edit /etc/openldap/slapd.access.conf
access to attrs=userPassword
by dn="cn=Manager,dc=systeminteg,dc=com" write
by self write
by anonymous auth
by * none
access to dn.base="" by * read
access to *
by dn="cn=Manager,dc=systeminteg,dc=com" write
by * read
# allow onlu rootdn to read the monitor
access to *
by dn.exact="cn=Manager,dc=systeminteg,dc=com" read
by * none
Edit /etc/syslog.conf
Add local4.* /var/log/slapd.log
Restart syslog:
service syslog restart
Start ldap:
service ldap start
slaptest
chown ldap:ldap –R /var/lib/ldap
Restart ldap:
service ldap restart
chkconfig ldap on
Testing
ldapsearch -x -D ‘cn=Manager,dc=systeminteg,dc=com" -W -s base ‘(onjectclass=*)’ namingContexts
Config authconfig-tui
Choose: Cache Information – Use MD5 Password – Use Shadow Passwords – Use LDAP Authentication – Local authorization is sufficient
Don’t check Use TLS – Server: ldap://192.168.1.1 – Base DN: dc=systeminteg,dc=com
Make an setup.ldif file
# — Start of file —
# Define the top level organization
dn: dc=systeminteg,dc=com
objectClass: dcObject
objectClass: organization
dc: systeminteg
o: SystemInteg
description: System Integration
# Create the organizational unit to hold users
dn: ou=People,dc=systeminteg,dc=com
objectClass: organizationalUnit
ou: People
# Create the organizational unit to hold groups
dn: ou=Group,dc=systeminteg,dc=com
objectClass: organizationalUnit
ou: Group
# Create the organizational units to hold machines
dn: ou=Hosts,dc=systeminteg,dc=com
objectClass: organizationalUnit
ou: Hosts
# Create the organizational unit to hold id mapping
dn: ou=Idmap,dc=systeminteg,dc=com
objectClass: organizationalUnit
ou: Idmap
# — End of file —
Add setup.ldif file
ldapadd -v -D "cn=Manager,dc=systeminteg,dc=com" -x -W -f setup.ldif
Restart Server
chkconfig ldap on
chkconfig nscd on
reboot
II.II Config Samba
Edit /etc/samba/smb.conf
[global]
workgroup = SYSTEMINTEG.COM
netbios name = PDC-SVR
passdb backend = ldapsam:"ldap://pdc-srv.systeminteg.com"
printcap name = cups
printing = cups
security = user
log level = 3
pam password change = yes
ldap ssl = off
ldap passwd sync = yes
ldap admin dn = cn=Manager,dc=systeminteg,dc=com
ldap suffix = dc=systeminteg,dc=com
ldap user suffix = ou=People
ldap group suffix = ou=Group
ldap idmap suffix = ou=Idmap
ldap machine suffix = ou=Hosts
ldap delete dn = Yes
add user script = /usr/sbin/smbldap-useradd -m "%u"
add machine script = /usr/sbin/smbldap-useradd -w "%u"
add group script = /usr/sbin/smbldap-groupadd -p "%g"
add user to group script = /usr/sbin/smbldap-groupmod -m "%u" "%g"
delete user from group script = /usr/sbin/smbldap-groupmod -x "%u" "%g"
set primary group script = /usr/sbin/smbldap-usermod -g "%g" "%u"
delete user script = /usr/sbin/smbldap-userdel "%u"
delete group script = /usr/sbin/smbldap-groupdel "%g"
logon path =
logon drive =
logon home =
#logon script = %U.bat
logon script = startup.bat
domain logons = Yes
os level = 35
preferred master = Yes
domain master = Yes
idmap uid = 15000-20000
idmap gid = 15000-20000
# passwd program = /usr/bin/passwd ‘%u’
unix password sync = no
passwd chat = "*New UNIX password*" %n\n "*Retype new UNIX password*" %n\n "*updated successfully*"
enable privileges = yes
username map = /etc/samba/smbusers
wins support = Yes
server signing = auto
server schannel = auto
#[homes]
#comment = Home Directories
#valid users = %S
#read only = No
#browseable = No
[netlogon]
comment = Network Logon Service
path = /var/lib/samba/netlogon
admin users = root Administrator admin
guest ok = Yes
browseable = No
admin users = Administrator
valid users = %U
#[Profiles]
#comment = Roaming Profile Share
#path = /var/lib/samba/profiles
#read only = No
#profile acls = Yes
#create mask = 0600
#directory mask = 0700
Edit /etc/samba/smbusers
# Unix_name = SMB_name1 SMB_name2 …
root = administrator Administrator admin
nobody = guest pcguest smbguest
testparm
smbpasswd –w {passLDAP}
service smb restart
service winbind restart
chkconfig smb on
chkconfig winbind on
II.III Config smbldap-tools
Get SID:
net getlocalsid
cd /usr/share/doc/smbldap-tools-0.9.6
./configure.pl
Show error
Use of $# is deprecated at configure.pl-org line 313.
Number found where operator expected at configure.pl-org line 527, near "#
Allows not to use smbpasswd (if with_smbpasswd="0"
(Might be a runaway multi-line "" string starting on line 313)
(Missing operator before 0?)
String found where operator expected at configure.pl-org line 532, near "#
Allows not to use slappasswd (if with_slappasswd=""
(Might be a runaway multi-line "" string starting on line 527)
(Missing semicolon on previous line?)
Number found where operator expected at configure.pl-org line 532, near "#
Allows not to use slappasswd (if with_slappasswd="0"
(Missing operator before 0?)
String found where operator expected at configure.pl-org line 539, near """
(Might be a runaway multi-line "" string starting on line 532)
(Missing semicolon on previous line?)
syntax error at configure.pl-org line 527, near "# Allows not to use
smbpasswd (if with_smbpasswd="0"
Execution of configure.pl-org aborted due to compilation errors.
Version-Release number of selected component (if applicable):
Name : smbldap-tools
Version : 0.9.6
Release : 1.el5
Source RPM : smbldap-tools-0.9.6-1.el5.src.rpm
How reproducible:
run perl configure.pl
Steps to Reproduce:
1. perl configure.pl
2.
3.
Actual results:
Expected results:
Additional info:
you can solve the problem:
at line 527
+# Allows not to use smbpasswd (if with_smbpasswd== 0 in smbldap.conf) but
-# Allows not to use smbpasswd (if with_smbpasswd="0" in smbldap.conf) but
at line 532
+# Allows not to use smbpasswd (if with_smbpasswd== 0 in smbldap.conf) but
-# Allows not to use smbpasswd (if with_smbpasswd="0" in smbldap.conf) but
./configure.pl
chmod 600 /etc/smbldap-tools/smbldap_bind.conf
smbldap-populate
mkdir –p /var/lib/samba/{netlogon,profiles}
chmod 2775 /var/lib/samba/profiles
chgrp ‘Domain Users’ /var/lib/samba/profiles
reboot
Testing
Add user: smbldap-useradd -a -m "test01"
Set password: smbldap-passwd test01
ldapsearch -b "ou=People,dc=systeminteg,dc=com" -x "(uid=test01)"
net groupmap list
Joint PDC into domain SYSTEMINTEG.COM
net rpc join -S PDC-SRV Administrator%pass
III. Config SSL/TLS
service ldap stop
cd /etc/pki/tls/misc
./CA -newca
Commonname: exactly hostname
openssl req -newkey rsa:1024 -nodes -keyout newreq.pem -out newreq.pem
./CA -sign
cd /etc/pki/CA
cp cacert.pem /etc/openldap/cacerts/cacert.pem
cd /etc/pki/tls/misc
mv newcert.pem /etc/openldap/cacerts/servercrt.pem
mv newreq.pem /etc/openldap/cacerts/serverkey.pem
chmod 400 /etc/openldap/cacerts/serverkey.pem
Edit /etc/openldap/lapd.conf
…
TLS_REQCERT demand
…
Edit /etc/openldap/slapd.conf
…
TLSCipherSuite HIGH:MEDIUM:+SSLv2
TLSCACertificateFile /etc/openldap/cacerts/cacert.pem
TLSCertificateFile /etc/openldap/cacerts/servercrt.pem
TLSCertificateKeyFile /etc/openldap/cacerts/serverkey.pem
TLSVerifyClient demand
…
chown ldap:ldap -R /etc/openldap/cacerts/
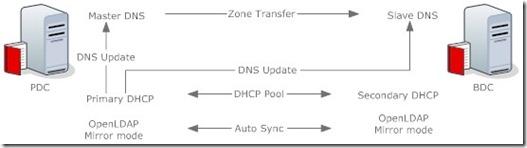
IV. Config OpenLDAP Mirror Mode
First comment out some lines in slapd.conf (Remember don’t put the space in front of lines)
modulepath /usr/lib64/openldap
moduleload syncprov.la
On Node 01
overlay syncprov
syncprov-checkpoint 100 10
syncprov-sessionlog 100
# Global section
serverID 1
# syncrepl directive
syncrepl rid=001
provider=ldap://192.168.1.2
bindmethod=simple
binddn="cn=Manager,dc=systeminteg,dc=com"
credentials={passLDAP}
searchbase="dc=systeminteg,dc=com"
schemachecking=on
type=refreshAndPersist
retry="60 +"
mirrormode on
On Node 02
overlay syncprov
syncprov-checkpoint 100 10
syncprov-sessionlog 100
# Global section
serverID 2
# syncrepl directive
syncrepl rid=001
provider=ldap://192.168.1.1
bindmethod=simple
binddn="cn=Manager,dc=systeminteg,dc=com"
credentials={passLDAP}
searchbase="dc=systeminteg,dc=com"
schemachecking=on
type=refreshAndPersist
retry="60 +"
mirrormode on
Remember move lines to the end of file slapd.conf
# enable monitoring
database monitor
Index:
/etc/openldap/slapd.conf
#
# See slapd.conf(5) for details on configuration options.
# This file should NOT be world readable.
#
include /etc/openldap/schema/corba.schema
include /etc/openldap/schema/core.schema
include /etc/openldap/schema/cosine.schema
include /etc/openldap/schema/duaconf.schema
include /etc/openldap/schema/dyngroup.schema
include /etc/openldap/schema/inetorgperson.schema
include /etc/openldap/schema/java.schema
include /etc/openldap/schema/misc.schema
include /etc/openldap/schema/nis.schema
include /etc/openldap/schema/openldap.schema
include /etc/openldap/schema/ppolicy.schema
include /etc/openldap/schema/collective.schema
include /etc/openldap/schema/samba.schema
include /etc/openldap/slapd.access.conf
# Allow LDAPv2 client connections. This is NOT the default.
allow bind_v2
# Do not enable referrals until AFTER you have a working directory
# service AND an understanding of referrals.
#referral ldap://root.openldap.org
pidfile /var/run/openldap/slapd.pid
argsfile /var/run/openldap/slapd.args
# Load dynamic backend modules:
modulepath /usr/lib64/openldap
# or /usr/lib64/openldap
#moduleload accesslog.la
# moduleload auditlog.la
# moduleload back_sql.la
# moduleload denyop.la
# moduleload dyngroup.la
# moduleload dynlist.la
# moduleload lastmod.la
# moduleload pcache.la
# moduleload ppolicy.la
# moduleload refint.la
# moduleload retcode.la
# moduleload rwm.la
moduleload syncprov.la
# moduleload translucent.la
# moduleload unique.la
# moduleload valsort.la
# The next three lines allow use of TLS for encrypting connections using a
# dummy test certificate which you can generate by changing to
# /etc/pki/tls/certs, running "make slapd.pem", and fixing permissions on
# slapd.pem so that the ldap user or group can read it. Your client software
# may balk at self-signed certificates, however.
# TLSCACertificateFile /etc/pki/tls/certs/ca-bundle.crt
# TLSCertificateFile /etc/pki/tls/certs/slapd.pem
# TLSCertificateKeyFile /etc/pki/tls/certs/slapd.pem
TLSCipherSuite HIGH:MEDIUM:+SSLv2
TLSCACertificateFile /etc/openldap/cacerts/cacert.pem
TLSCertificateFile /etc/openldap/cacerts/servercrt.pem
TLSCertificateKeyFile /etc/openldap/cacerts/serverkey.pem
TLSVerifyClient demand
# Sample security restrictions
# Require integrity protection (prevent hijacking)
# Require 112-bit (3DES or better) encryption for updates
# Require 63-bit encryption for simple bind
# security ssf=1 update_ssf=112 simple_bind=64
# Sample access control policy:
# Root DSE: allow anyone to read it
# Subschema (sub)entry DSE: allow anyone to read it
# Other DSEs:
# Allow self write access
# Allow authenticated users read access
# Allow anonymous users to authenticate
# Directives needed to implement policy:
# access to dn.base="" by * read
# access to dn.base="cn=Subschema" by * read
# access to *
# by self write
# by users read
# by anonymous auth
#
# if no access controls are present, the default policy
# allows anyone and everyone to read anything but restricts
# updates to rootdn. (e.g., "access to * by * read")
#
# rootdn can always read and write EVERYTHING!
#######################################################################
# ldbm and/or bdb database definitions
#######################################################################
database bdb
suffix "dc=systeminteg,dc=com"
checkpoint 1024 15
rootdn "cn=Manager,dc=systeminteg,dc=com"
# Cleartext passwords, especially for the rootdn, should
# be avoided. See slappasswd(8) and slapd.conf(5) for details.
# Use of strong authentication encouraged.
# rootpw secret
# rootpw {crypt}ijFYNcSNctBYg
rootpw {passLDAP}
# The database directory MUST exist prior to running slapd AND
# should only be accessible by the slapd and slap tools.
# Mode 700 recommended.
directory /var/lib/ldap
loglevel 256
# Indices to maintain for this database
index objectClass eq,pres
index ou,cn,mail,surname,givenname eq,pres,sub
index uidNumber,gidNumber,loginShell eq,pres
index uid,memberUid eq,pres,sub
index nisMapName,nisMapEntry eq,pres,sub
index entryUUID,entryCSN eq
index sambaSIDList eq
index sambaGroupType eq
index sambaSID eq
# Replicas of this database
#replogfile /var/lib/ldap/openldap-master-replog
#replica host=ldap-1.example.com:389 starttls=critical
# bindmethod=sasl saslmech=GSSAPI
# authcId=host/ldap-master.example.com@EXAMPLE.COM
# allow onlu rootdn to read the monitor
#access to *
# by dn.exact="cn=Manager,dc=my-domain,dc=com" read
# by * none
overlay syncprov
syncprov-checkpoint 100 10
syncprov-sessionlog 100
# Global section
serverID 1
# syncrepl directive
syncrepl rid=001
provider=ldap://192.168.1.2
bindmethod=simple
binddn="cn=Manager,dc=systeminteg,dc=com"
credentials={passLDAP}
searchbase="dc=systeminteg,dc=com"
schemachecking=on
type=refreshAndPersist
retry="60 +"
mirrormode on
# enable monitoring
database monitor
/etc/openldap/ldap.conf
#
# LDAP Defaults
#
# See ldap.conf(5) for details
# This file should be world readable but not world writable.
#BASE dc=example, dc=com
#URI ldap://ldap.example.com ldap://ldap-master.example.com:666
#SIZELIMIT 12
#TIMELIMIT 15
#DEREF never
URI ldap://192.168.1.1
BASE dc=systeminteg,dc=com
TLS_CACERTDIR /etc/openldap/cacerts
/etc/ldap.conf
# @(#)$Id: ldap.conf,v 1.38 2006/05/15 08:13:31 lukeh Exp $
#
# This is the configuration file for the LDAP nameservice
# switch library and the LDAP PAM module.
#
# The man pages for this file are nss_ldap(5) and pam_ldap(5)
#
# PADL Software
# http://www.padl.com
#
# Your LDAP server. Must be resolvable without using LDAP.
# Multiple hosts may be specified, each separated by a
# space. How long nss_ldap takes to failover depends on
# whether your LDAP client library supports configurable
# network or connect timeouts (see bind_timelimit).
#host 127.0.0.1
host 192.168.1.1
# The distinguished name of the search base.
base dc=systeminteg,dc=com
# Another way to specify your LDAP server is to provide an
# uri with the server name. This allows to use
# Unix Domain Sockets to connect to a local LDAP Server.
#uri ldap://127.0.0.1/
#uri ldaps://127.0.0.1/
#uri ldapi://%2fvar%2frun%2fldapi_sock/
# Note: %2f encodes the ‘/’ used as directory separator
# The LDAP version to use (defaults to 3
# if supported by client library)
#ldap_version 3
# The distinguished name to bind to the server with.
# Optional: default is to bind anonymously.
#binddn cn=proxyuser,dc=example,dc=com
# The credentials to bind with.
# Optional: default is no credential.
#bindpw secret
# The distinguished name to bind to the server with
# if the effective user ID is root. Password is
# stored in /etc/ldap.secret (mode 600)
#rootbinddn cn=manager,dc=example,dc=com
# The port.
# Optional: default is 389.
#port 389
# The search scope.
#scope sub
#scope one
#scope base
# Search timelimit
#timelimit 30
timelimit 120
# Bind/connect timelimit
#bind_timelimit 30
bind_timelimit 120
# Reconnect policy: hard (default) will retry connecting to
# the software with exponential backoff, soft will fail
# immediately.
#bind_policy hard
# Idle timelimit; client will close connections
# (nss_ldap only) if the server has not been contacted
# for the number of seconds specified below.
#idle_timelimit 3600
idle_timelimit 3600
# Filter to AND with uid=%s
#pam_filter objectclass=account
# The user ID attribute (defaults to uid)
#pam_login_attribute uid
# Search the root DSE for the password policy (works
# with Netscape Directory Server)
#pam_lookup_policy yes
# Check the ‘host’ attribute for access control
# Default is no; if set to yes, and user has no
# value for the host attribute, and pam_ldap is
# configured for account management (authorization)
# then the user will not be allowed to login.
#pam_check_host_attr yes
# Check the ‘authorizedService’ attribute for access
# control
# Default is no; if set to yes, and the user has no
# value for the authorizedService attribute, and
# pam_ldap is configured for account management
# (authorization) then the user will not be allowed
# to login.
#pam_check_service_attr yes
# Group to enforce membership of
#pam_groupdn cn=PAM,ou=Groups,dc=example,dc=com
# Group member attribute
#pam_member_attribute uniquemember
# Specify a minium or maximum UID number allowed
#pam_min_uid 0
#pam_max_uid 0
# Template login attribute, default template user
# (can be overriden by value of former attribute
# in user’s entry)
#pam_login_attribute userPrincipalName
#pam_template_login_attribute uid
#pam_template_login nobody
# HEADS UP: the pam_crypt, pam_nds_passwd,
# and pam_ad_passwd options are no
# longer supported.
#
# Do not hash the password at all; presume
# the directory server will do it, if
# necessary. This is the default.
#pam_password clear
# Hash password locally; required for University of
# Michigan LDAP server, and works with Netscape
# Directory Server if you’re using the UNIX-Crypt
# hash mechanism and not using the NT Synchronization
# service.
#pam_password crypt
# Remove old password first, then update in
# cleartext. Necessary for use with Novell
# Directory Services (NDS)
#pam_password clear_remove_old
#pam_password nds
# RACF is an alias for the above. For use with
# IBM RACF
#pam_password racf
# Update Active Directory password, by
# creating Unicode password and updating
# unicodePwd attribute.
#pam_password ad
# Use the OpenLDAP password change
# extended operation to update the password.
#pam_password exop
# Redirect users to a URL or somesuch on password
# changes.
#pam_password_prohibit_message Please visit http://internal to change your password.
# RFC2307bis naming contexts
# Syntax:
# nss_base_XXX base?scope?filter
# where scope is {base,one,sub}
# and filter is a filter to be &’d with the
# default filter.
# You can omit the suffix eg:
# nss_base_passwd ou=People,
# to append the default base DN but this
# may incur a small performance impact.
#nss_base_passwd ou=People,dc=example,dc=com?one
#nss_base_shadow ou=People,dc=example,dc=com?one
#nss_base_group ou=Group,dc=example,dc=com?one
#nss_base_hosts ou=Hosts,dc=example,dc=com?one
#nss_base_services ou=Services,dc=example,dc=com?one
#nss_base_networks ou=Networks,dc=example,dc=com?one
#nss_base_protocols ou=Protocols,dc=example,dc=com?one
#nss_base_rpc ou=Rpc,dc=example,dc=com?one
#nss_base_ethers ou=Ethers,dc=example,dc=com?one
#nss_base_netmasks ou=Networks,dc=example,dc=com?ne
#nss_base_bootparams ou=Ethers,dc=example,dc=com?one
#nss_base_aliases ou=Aliases,dc=example,dc=com?one
#nss_base_netgroup ou=Netgroup,dc=example,dc=com?one
# Just assume that there are no supplemental groups for these named users
nss_initgroups_ignoreusers root,ldap,named,avahi,haldaemon,dbus,radvd,tomcat,radiusd,news,mailman,nscd,gdm
# attribute/objectclass mapping
# Syntax:
#nss_map_attribute rfc2307attribute mapped_attribute
#nss_map_objectclass rfc2307objectclass mapped_objectclass
# configure –enable-nds is no longer supported.
# NDS mappings
#nss_map_attribute uniqueMember member
# Services for UNIX 3.5 mappings
#nss_map_objectclass posixAccount User
#nss_map_objectclass shadowAccount User
#nss_map_attribute uid msSFU30Name
#nss_map_attribute uniqueMember msSFU30PosixMember
#nss_map_attribute userPassword msSFU30Password
#nss_map_attribute homeDirectory msSFU30HomeDirectory
#nss_map_attribute homeDirectory msSFUHomeDirectory
#nss_map_objectclass posixGroup Group
#pam_login_attribute msSFU30Name
#pam_filter objectclass=User
#pam_password ad
# configure –enable-mssfu-schema is no longer supported.
# Services for UNIX 2.0 mappings
#nss_map_objectclass posixAccount User
#nss_map_objectclass shadowAccount user
#nss_map_attribute uid msSFUName
#nss_map_attribute uniqueMember posixMember
#nss_map_attribute userPassword msSFUPassword
#nss_map_attribute homeDirectory msSFUHomeDirectory
#nss_map_attribute shadowLastChange pwdLastSet
#nss_map_objectclass posixGroup Group
#nss_map_attribute cn msSFUName
#pam_login_attribute msSFUName
#pam_filter objectclass=User
#pam_password ad
# RFC 2307 (AD) mappings
#nss_map_objectclass posixAccount user
#nss_map_objectclass shadowAccount user
#nss_map_attribute uid sAMAccountName
#nss_map_attribute homeDirectory unixHomeDirectory
#nss_map_attribute shadowLastChange pwdLastSet
#nss_map_objectclass posixGroup group
#nss_map_attribute uniqueMember member
#pam_login_attribute sAMAccountName
#pam_filter objectclass=User
#pam_password ad
# configure –enable-authpassword is no longer supported
# AuthPassword mappings
#nss_map_attribute userPassword authPassword
# AIX SecureWay mappings
#nss_map_objectclass posixAccount aixAccount
#nss_base_passwd ou=aixaccount,?one
#nss_map_attribute uid userName
#nss_map_attribute gidNumber gid
#nss_map_attribute uidNumber uid
#nss_map_attribute userPassword passwordChar
#nss_map_objectclass posixGroup aixAccessGroup
#nss_base_group ou=aixgroup,?one
#nss_map_attribute cn groupName
#nss_map_attribute uniqueMember member
#pam_login_attribute userName
#pam_filter objectclass=aixAccount
#pam_password clear
# Netscape SDK LDAPS
#ssl on
# Netscape SDK SSL options
#sslpath /etc/ssl/certs
# OpenLDAP SSL mechanism
# start_tls mechanism uses the normal LDAP port, LDAPS typically 636
#ssl start_tls
#ssl on
# OpenLDAP SSL options
# Require and verify server certificate (yes/no)
# Default is to use libldap’s default behavior, which can be configured in
# /etc/openldap/ldap.conf using the TLS_REQCERT setting. The default for
# OpenLDAP 2.0 and earlier is "no", for 2.1 and later is "yes".
#tls_checkpeer yes
# CA certificates for server certificate verification
# At least one of these are required if tls_checkpeer is "yes"
#tls_cacertfile /etc/ssl/ca.cert
#tls_cacertdir /etc/ssl/certs
# Seed the PRNG if /dev/urandom is not provided
#tls_randfile /var/run/egd-pool
# SSL cipher suite
# See man ciphers for syntax
#tls_ciphers TLSv1
# Client certificate and key
# Use these, if your server requires client authentication.
#tls_cert
#tls_key
# Disable SASL security layers. This is needed for AD.
#sasl_secprops maxssf=0
# Override the default Kerberos ticket cache location.
#krb5_ccname FILE:/etc/.ldapcache
# SASL mechanism for PAM authentication – use is experimental
# at present and does not support password policy control
#pam_sasl_mech DIGEST-MD5
uri ldap://192.168.1.1
ssl no
tls_cacertdir /etc/openldap/cacerts
pam_password md5
/etc/samba/smb.conf
[global]
workgroup = SYSTEMINTEG.COM
netbios name = PDC-SVR
passdb backend = ldapsam:"ldap://pdc-srv.systeminteg.com"
printcap name = cups
printing = cups
security = user
log level = 3
pam password change = yes
ldap ssl = off
ldap passwd sync = yes
ldap admin dn = cn=Manager,dc=systeminteg,dc=com
ldap suffix = dc=systeminteg,dc=com
ldap user suffix = ou=People
ldap group suffix = ou=Group
ldap idmap suffix = ou=Idmap
ldap machine suffix = ou=Hosts
ldap delete dn = Yes
add user script = /usr/sbin/smbldap-useradd -m "%u"
add machine script = /usr/sbin/smbldap-useradd -w "%u"
add group script = /usr/sbin/smbldap-groupadd -p "%g"
add user to group script = /usr/sbin/smbldap-groupmod -m "%u" "%g"
delete user from group script = /usr/sbin/smbldap-groupmod -x "%u" "%g"
set primary group script = /usr/sbin/smbldap-usermod -g "%g" "%u"
delete user script = /usr/sbin/smbldap-userdel "%u"
delete group script = /usr/sbin/smbldap-groupdel "%g"
logon path =
logon drive =
logon home =
#logon script = %U.bat
logon script = startup.bat
domain logons = Yes
os level = 35
preferred master = Yes
domain master = Yes
idmap uid = 15000-20000
idmap gid = 15000-20000
# passwd program = /usr/bin/passwd ‘%u’
unix password sync = no
passwd chat = "*New UNIX password*" %n\n "*Retype new UNIX password*" %n\n "*updated successfully*"
enable privileges = yes
username map = /etc/samba/smbusers
wins support = Yes
server signing = auto
server schannel = auto
#[homes]
#comment = Home Directories
#valid users = %S
#read only = No
#browseable = No
[netlogon]
comment = Network Logon Service
path = /var/lib/samba/netlogon
admin users = root Administrator admin
guest ok = Yes
browseable = No
admin users = Administrator
valid users = %U
#[Profiles]
#comment = Roaming Profile Share
#path = /var/lib/samba/profiles
#read only = No
#profile acls = Yes
#create mask = 0600
#directory mask = 0700
/etc/samba/smbusers
# Unix_name = SMB_name1 SMB_name2 …
root = administrator Administrator admin
nobody = guest pcguest smbguest
/etc/smbldap-tools/smbldap.conf
# $Source: /opt/cvs/samba/smbldap-tools/configure.pl,v
# smbldap-tools.conf : Q & D configuration file for smbldap-tools
# This code was developped by IDEALX (http://IDEALX.org/) and
# contributors (their names can be found in the CONTRIBUTORS file).
#
# Copyright (C) 2001-2002 IDEALX
#
# This program is free software; you can redistribute it and/or
# modify it under the terms of the GNU General Public License
# as published by the Free Software Foundation; either version 2
# of the License, or (at your option) any later version.
#
# This program is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License
# along with this program; if not, write to the Free Software
# Foundation, Inc., 59 Temple Place – Suite 330, Boston, MA 02111-1307,
# USA.
# Purpose :
# . be the configuration file for all smbldap-tools scripts
##############################################################################
#
# General Configuration
#
##############################################################################
# Put your own SID. To obtain this number do: "net getlocalsid".
# If not defined, parameter is taking from "net getlocalsid" return
SID="S-1-5-21-2238024752-698867721-3687915981"
# Domain name the Samba server is in charged.
# If not defined, parameter is taking from smb.conf configuration file
# Ex: sambaDomain="IDEALX-NT"
sambaDomain="SYSTEMINTEG.COM"
##############################################################################
#
# LDAP Configuration
#
##############################################################################
# Notes: to use to dual ldap servers backend for Samba, you must patch
# Samba with the dual-head patch from IDEALX. If not using this patch
# just use the same server for slaveLDAP and masterLDAP.
# Those two servers declarations can also be used when you have
# . one master LDAP server where all writing operations must be done
# . one slave LDAP server where all reading operations must be done
# (typically a replication directory)
# Slave LDAP server
# Ex: slaveLDAP=127.0.0.1
# If not defined, parameter is set to "127.0.0.1"
slaveLDAP="192.168.1.2"
# Slave LDAP port
# If not defined, parameter is set to "389"
slavePort="389"
# Master LDAP server: needed for write operations
# Ex: masterLDAP=127.0.0.1
# If not defined, parameter is set to "127.0.0.1"
masterLDAP="192.168.1.1"
# Master LDAP port
# If not defined, parameter is set to "389"
masterPort="389"
# Use TLS for LDAP
# If set to 1, this option will use start_tls for connection
# (you should also used the port 389)
# If not defined, parameter is set to "1"
ldapTLS="0"
# How to verify the server’s certificate (none, optional or require)
# see "man Net::LDAP" in start_tls section for more details
verify=""
# CA certificate
# see "man Net::LDAP" in start_tls section for more details
cafile=""
# certificate to use to connect to the ldap server
# see "man Net::LDAP" in start_tls section for more details
clientcert=""
# key certificate to use to connect to the ldap server
# see "man Net::LDAP" in start_tls section for more details
clientkey=""
# LDAP Suffix
# Ex: suffix=dc=IDEALX,dc=ORG
suffix="dc=systeminteg,dc=com"
# Where are stored Users
# Ex: usersdn="ou=Users,dc=IDEALX,dc=ORG"
# Warning: if ‘suffix’ is not set here, you must set the full dn for usersdn
usersdn="ou=People,${suffix}"
# Where are stored Computers
# Ex: computersdn="ou=Computers,dc=IDEALX,dc=ORG"
# Warning: if ‘suffix’ is not set here, you must set the full dn for computersdn
computersdn="ou=Hosts,${suffix}"
# Where are stored Groups
# Ex: groupsdn="ou=Groups,dc=IDEALX,dc=ORG"
# Warning: if ‘suffix’ is not set here, you must set the full dn for groupsdn
groupsdn="ou=Group,${suffix}"
# Where are stored Idmap entries (used if samba is a domain member server)
# Ex: groupsdn="ou=Idmap,dc=IDEALX,dc=ORG"
# Warning: if ‘suffix’ is not set here, you must set the full dn for idmapdn
idmapdn="ou=Idmap,${suffix}"
# Where to store next uidNumber and gidNumber available for new users and groups
# If not defined, entries are stored in sambaDomainName object.
# Ex: sambaUnixIdPooldn="sambaDomainName=${sambaDomain},${suffix}"
# Ex: sambaUnixIdPooldn="cn=NextFreeUnixId,${suffix}"
sambaUnixIdPooldn="sambaDomainName=SYSTEMINTEG.COM,${suffix}"
# Default scope Used
scope="sub"
# Unix password encryption (CRYPT, MD5, SMD5, SSHA, SHA, CLEARTEXT)
hash_encrypt="SSHA"
# if hash_encrypt is set to CRYPT, you may set a salt format.
# default is "%s", but many systems will generate MD5 hashed
# passwords if you use "$1$%.8s". This parameter is optional!
crypt_salt_format=""
##############################################################################
#
# Unix Accounts Configuration
#
##############################################################################
# Login defs
# Default Login Shell
# Ex: userLoginShell="/bin/bash"
userLoginShell="/bin/bash"
# Home directory
# Ex: userHome="/home/%U"
userHome="/home/%U"
# Default mode used for user homeDirectory
userHomeDirectoryMode="700"
# Gecos
userGecos="System User"
# Default User (POSIX and Samba) GID
defaultUserGid="513"
# Default Computer (Samba) GID
defaultComputerGid="515"
# Skel dir
skeletonDir="/etc/skel"
# Default password validation time (time in days) Comment the next line if
# you don’t want password to be enable for defaultMaxPasswordAge days (be
# careful to the sambaPwdMustChange attribute’s value)
defaultMaxPasswordAge="45"
##############################################################################
#
# SAMBA Configuration
#
##############################################################################
# The UNC path to home drives location (%U username substitution)
# Just set it to a null string if you want to use the smb.conf ‘logon home’
# directive and/or disable roaming profiles
# Ex: userSmbHome="\\PDC-SMB3\%U"
userSmbHome=""
# The UNC path to profiles locations (%U username substitution)
# Just set it to a null string if you want to use the smb.conf ‘logon path’
# directive and/or disable roaming profiles
# Ex: userProfile="\\PDC-SMB3\profiles\%U"
userProfile=""
# The default Home Drive Letter mapping
# (will be automatically mapped at logon time if home directory exist)
# Ex: userHomeDrive="H:"
userHomeDrive=""
# The default user netlogon script name (%U username substitution)
# if not used, will be automatically username.cmd
# make sure script file is edited under dos
# Ex: userScript="startup.cmd" # make sure script file is edited under dos
userScript="logon.bat"
# Domain appended to the users "mail"-attribute
# when smbldap-useradd -M is used
# Ex: mailDomain="idealx.com"
mailDomain="systeminteg.com"
##############################################################################
#
# SMBLDAP-TOOLS Configuration (default are ok for a RedHat)
#
##############################################################################
# Allows not to use smbpasswd (if with_smbpasswd== 0 in smbldap.conf) but
# prefer Crypt::SmbHash library
with_smbpasswd="0"
smbpasswd="/usr/bin/smbpasswd"
# Allows not to use slappasswd (if with_slappasswd== 0 in smbldap.conf)
# but prefer Crypt:: libraries
with_slappasswd="0"
slappasswd="/usr/sbin/slappasswd"
# comment out the following line to get rid of the default banner
# no_banner="1"
/etc/smbldap-tools/smbldap_bind
############################
# Credential Configuration #
############################
# Notes: you can specify two differents configuration if you use a
# master ldap for writing access and a slave ldap server for reading access
# By default, we will use the same DN (so it will work for standard Samba
# release)
slaveDN="cn=Manager,dc=systeminteg,dc=com"
slavePw="passLDAP"
masterDN="cn=Manager,dc=systeminteg,dc=com"
masterPw="passLDAP"